Cybersecurity Challenges in Software-Defined Buses
Software-defined buses face rising cyber threats, highlighted by Norway’s 850-bus OTA vulnerability. Explore real attacks on transit systems, expanding attack surfaces, R155/R156 regulatory requirements, and advanced defense strategies to protect connected and electric bus fleets.
SDVTOP POST


"Connected Buses,
Connected Risks,
Secure
the Fleet Before
It's Too Late."
Norwegian Mountain Facility: Inside a mountain bunker designed to block all external signals, cybersecurity experts from Telenor Group and the University of South-Eastern Norway conducted controlled tests on electric buses during the summer of 2025. Their discovery sent shockwaves through European transit systems: approximately 850 Yutong electric buses operating across Norway could theoretically be remotely disabled through their over-the-air update systems. While no actual attacks occurred, the vulnerability was real — and once it was publicly revealed in early November 2025, investigations were immediately launched across Denmark, the UK, and Australia.
This wasn't a theoretical research paper or conference presentation. It was a real-world demonstration that software-defined buses, for all their operational advantages, had become potential targets for remote manipulation. The incident crystallized a truth that the transit industry could no longer ignore: as buses evolve into connected, software-driven platforms, cybersecurity transforms from IT concern to life-safety imperative.
The global vehicle cybersecurity market, valued at approximately $3.15 billion in 2020, is projected to reach $16.2 billion by 2035, reflecting an 18.7% compound annual growth rate. This explosive growth underscores the escalating demand for robust security frameworks as buses become increasingly connected and software-dependent.
But here's the critical challenge: How do you defend vehicles that are simultaneously safety-critical infrastructure, mobile computing platforms, and public-facing services? How do you balance the operational benefits of connectivity against the existential risks of compromise?
The Real-World Wake-Up Calls: When Theory Became Reality
850
Yutong buses found vulnerable in Norway (Nov 2024)
$4.4M
Average data breach cost in transportation sector (IBM 2024)
$16.2B
Global vehicle cybersecurity market by 2035
500+
VicOne Cybersecurity Competition participants (2025)
Case Study: The Yutong Vulnerability Discovery
The Setup:
• 850 Yutong electric buses operating across Norway
• Cloud-integrated OTA update systems
• Manufacturer direct digital access for battery management, diagnostics
• Tests conducted in signal-blocking mountain facility


The Vulnerability:
• Theoretical remote shutdown capability identified
• OTA update channels provided manufacturer access to critical systems
• While Yutong maintained "no physical connection" to steering/braking, the incident exposed risks
• Investigations launched across Europe and Australia
"As buses incorporate more integrated technologies, we have a technological window of time to implement necessary security measures right now."
— Bernt Reitan Jenssen, CEO, Ruter
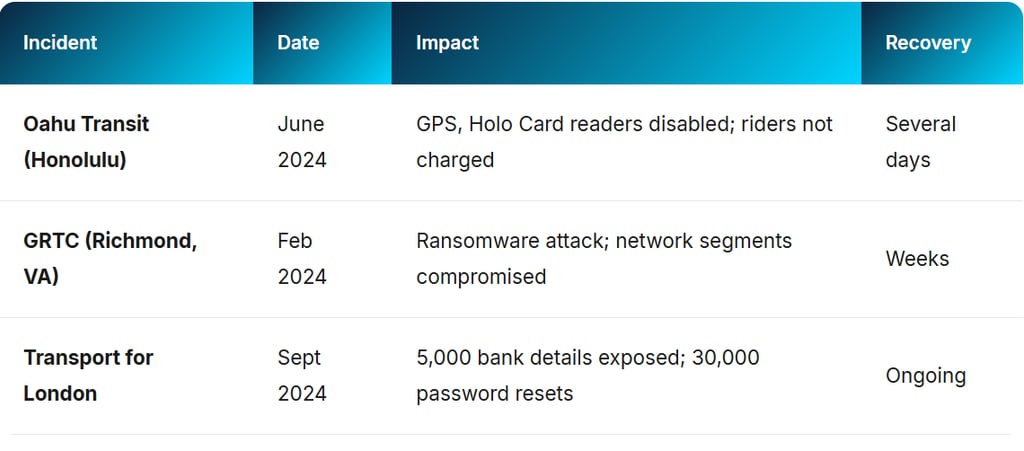
US Transit System Breaches: The Operational Disruption Reality
While the Norwegian discovery was theoretical, US transit systems experienced actual operational impacts:
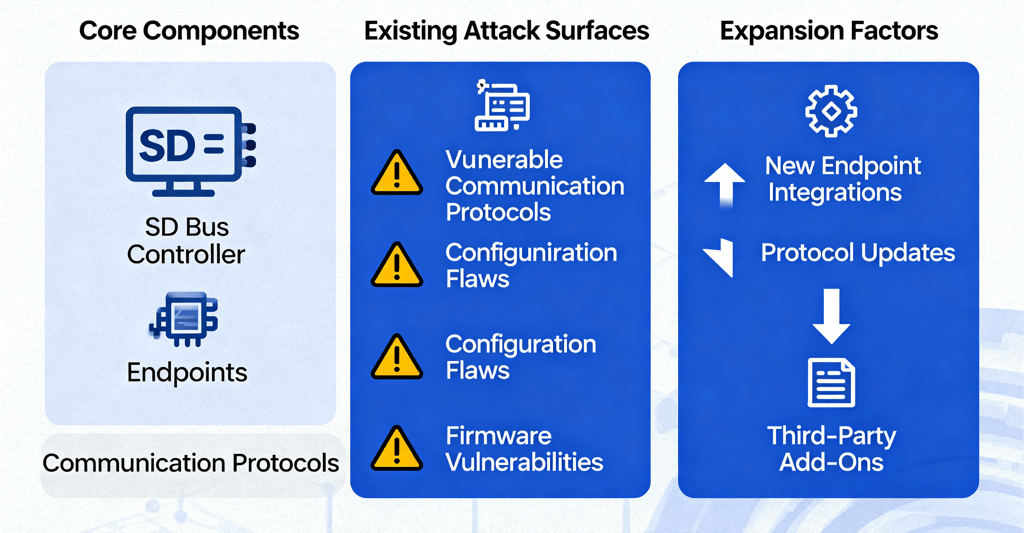
The Expanding Attack Surface: Where Vulnerabilities Hide
Modern software-defined buses present threat actors with multiple entry points. The increased connectivity creates numerous access points into internal vehicle networks, each presenting multiple software vulnerabilities that adversaries can exploit.
November 2025: Norwegian Transport Operator Ruter's Discovery




The Ripple Effect:
• Denmark's Movia: Immediate investigation of 469 Chinese-made electric buses (262 Yutong models)
• United Kingdom: Scrutiny of approximately 700 Yutong buses nationwide
• Australia: Review of fleet security protocols initiated
• Regulatory response: Accelerated EU cybersecurity compliance timelines
These weren't sophisticated nation-state attacks. They were opportunistic ransomware and phishing campaigns that succeeded because transit systems presented soft targets with inadequate defenses.
Passenger Wi-Fi: The Trojan Horse
Cybersecurity research demonstrated how attackers could use a bus's guest Wi-Fi to access and compromise critical systems. The attack chain:
Step 1: Connect to public bus Wi-Fi (no authentication required)
Step 2: Exploit vulnerabilities in IoT gateway separating networks
Step 3: Lateral movement to telematics gateway unit (TGU)
Step 4: Access CAN bus—the vehicle's nervous system
Step 5: Inject malicious commands affecting steering, braking, transmission
Implication: Without strong encryption and network segmentation, passenger convenience features become attack vectors into safety-critical systems.
Over-the-Air Update Channels: Double-Edged Sword
OTA updates enable operational efficiency—but also create persistent remote access channels. Compromise points include:
Source code repositories: Attackers infiltrating development environments
Open-source dependencies: Malicious code in third-party libraries
Software update servers: Man-in-the-middle attacks during transmission
Voltage fault injection: Hardware attacks on chipmaker processors
2021 Near-Miss: European agency's fleet management system compromised via contractor phishing. Attackers gained OTA server access. If deployed, 340 buses could have been disabled during rush hour. Prevented loss: €15M+.
Supply Chain Vulnerabilities: The Hidden Time Bomb
The automotive supply chain has become a prime target. McKinsey projects connectivity services could add up to $1.5 trillion by 2030. However, vulnerabilities compound risks:
Subsystem integration risk: Modern 12m bus contains components from 15-25 suppliers
Firmware backdoors: Malicious code inserted at component level
Legacy protocol vulnerabilities: HVAC, lighting using decades-old protocols
Update complexity: Each supplier's components on different schedules
Attack Surface Expansion in Software-Defined Buses
Regulatory Frameworks: From Voluntary to Mandatory
Recognition of these threats has spurred aggressive regulatory action worldwide. The era of "security through obscurity" has ended—replaced by mandated cybersecurity management systems and continuous compliance verification.
"Our vehicles are equipped with cybersecurity management systems from the design phase to detect, prevent, and respond to cyber threats. These systems continuously monitor potential cyberattacks, alert operators, and deploy countermeasures to neutralize attacks."
— Philippe Grand, Bus Digital Product Manager, Iveco Bus
UNECE R155/R156: The European Foundation
UNECE Regulation 155 (Cybersecurity Management System) and Regulation 156 (Software Update Management System) entered into force in January 2021. In the European Union, these regulations became mandatory for all new vehicle types from July 2022 and mandatory for all new vehicles produced from July 2024.
R155 Requirements include:
Risk-based cybersecurity system spanning vehicle's entire lifecycle (design → production → operation → decommissioning)
Protection of safety-critical functions: Type-approval authorities verify ECUs affecting safety cannot be compromised via external connectivity
Vulnerability management: Continuous monitoring, incident response, remediation tracking
Supply chain security: Assessment of supplier cybersecurity practices
Iveco Bus Implementation: With over 10,000 connected buses and coaches, Iveco achieved comprehensive R155 compliance including:
Cybersecurity measures integrated from design phase
Electrical/electronic units protected by mechanical locking + secure gateway
Penetration testing, security audits, third-party certifications
Software update management ensuring protection against emerging threats
US Department of Commerce Regulations
In January 2025, the US Department of Commerce finalized regulations establishing strict prohibitions against the import and sale of connected vehicle components containing Vehicle Connectivity System or Automated Driving System technologies with ties to China or Russia.
While initially focused on passenger vehicles under 10,001 pounds, a separate rule addressing connected commercial vehicles, including buses, is anticipated. The rationale: software-defined vehicles represent potential national security risks if compromised at scale.
EU Cyber Resilience Act: The Financial Hammer
The EU's Cyber Resilience Act and ISO/SAE 21434 compliance have become essential, with companies facing fines of up to €15 million or 2.5% of global turnover for non-compliance.
This transforms cybersecurity from "best practice" to "business-critical compliance requirement" with existential financial implications for non-compliant OEMs.
Technical Mitigation Strategies: Defense in Depth
Defending software-defined buses requires a multi-layered approach combining architectural isolation, continuous monitoring, and zero-trust principles. No single technology solves the problem—comprehensive defense requires orchestrated systems.
1 . System Segmentation: Preventing Cascade Failures
The software-defined vehicle approach offers advantages in preventing system-wide breakdowns because hardware and software are separated. Since each system is isolated—for example, the engine management system does not directly interact with the infotainment system—if one is attacked, the problem cannot automatically spread to the rest of the vehicle.
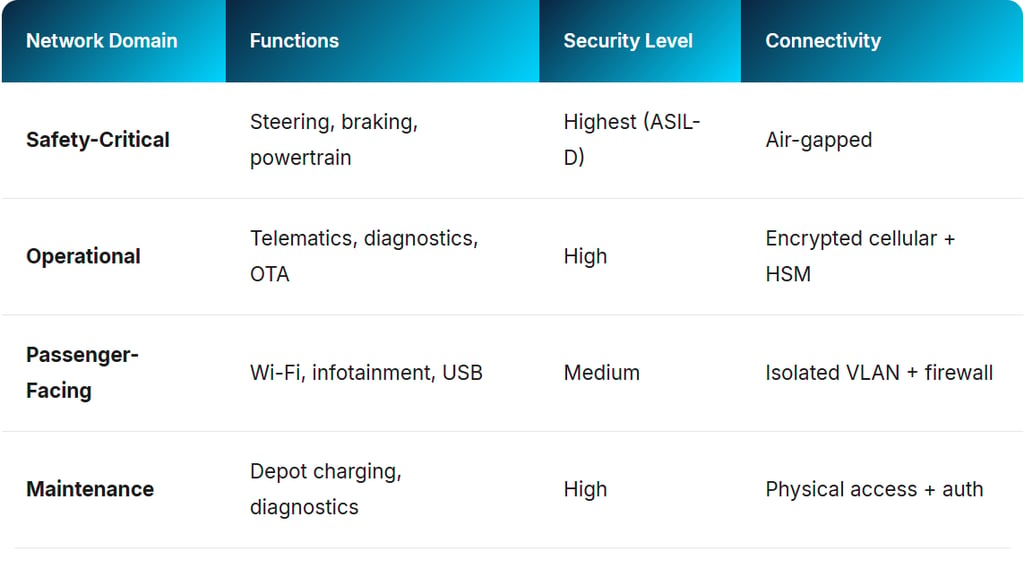
2 . Hardware Security Foundations
Hardware components — including microcontrollers, sensors, and communications modules — must be rigorously evaluated against industry standards to ensure that critical security features are present and that the system is resistant to tampering or unauthorized access. As buses evolve into software-defined, connected platforms, securing the hardware layer becomes essential: it is the trust anchor upon which all higher-level protections depend.
Key Technologies :
Hardware Security Modules (HSMs)
HSMs provide tamper-resistant environments where sensitive cryptographic operations — such as key generation, secure boot validation, and message authentication — can be executed safely. By isolating keys and enforcing access controls at the hardware level, HSMs reduce the risk of key extraction and firmware manipulation, two vectors commonly exploited in OTA-based attacks.
Trusted Execution Environments (TEEs)
TEEs create isolated zones within processors that ensure integrity and confidentiality for critical functions. In a software-defined bus, TEEs protect functions such as diagnostics, powertrain commands, and sensor fusion processes against malware or rogue applications.
Secure Boot and Secure Firmware Update
Secure Boot ensures that only authenticated and untampered firmware can run on the system. Coupled with cryptographically validated OTA updates, it prevents attackers from injecting malicious firmware — a scenario that has become increasingly plausible as vehicles rely more heavily on remote updates.
Physical Tamper Detection and Anti-Rollback Mechanisms
These mechanisms ensure that attempts to physically access control modules are logged or blocked, and that devices cannot be downgraded to older, more vulnerable software versions.
Practical Limitations (Addressed Briefly)
While hardware security provides the strongest chain of trust, it comes with constraints. HSMs and TEEs can introduce cost and integration overhead; legacy systems may lack compatibility; and their effectiveness depends on secure supply-chain practices — an area where gaps are still common. However, despite these challenges, hardware-anchored security remains one of the most reliable defenses against sophisticated compromise of fleet-wide bus systems.
3 . Continuous Monitoring and Threat Detection
Even with strong hardware and network segmentation, modern buses require active monitoring. Continuous threat detection — through anomaly detection systems, CAN-bus intrusion detection, and cloud-based analytics — enables operators to detect abnormal behavior early, whether it comes from compromised ECUs, unauthorized OTA activity, or misconfigured network components.
Fleet operators can integrate bus telemetry, vehicle logs, and OTA update histories into centralized dashboards, creating a real-time overview of operational health and emerging threats. This approach minimizes downtime, provides early warnings, and supports rapid incident response.
4. Supply Chain and Lifecycle Security
Securing a software-defined bus is not limited to the vehicle itself. Each supplier of sensors, telematics units, OTA systems, and ECUs must demonstrate secure development practices and verifiable firmware integrity. Lifecycle security — from design to decommissioning — ensures that vulnerabilities are not introduced through third-party libraries, outdated firmware components, or unsecured manufacturing processes.
Risk-based supplier assessment, SBOMs (Software Bills of Materials), and mandatory vulnerability disclosure programs increase transparency and reduce the probability of unnoticed flaws propagating into the fleet.
Conclusion
The discovery of remotely exploitable vulnerabilities in Yutong buses illustrates a broader reality: as transit vehicles become software-defined, their attack surface expands dramatically. Protecting these systems requires a layered security model that integrates hardware trust anchors, network segmentation, secure OTA processes, and continuous monitoring — all aligned with regulatory frameworks such as UNECE R155/R156.
While limitations exist — from integration challenges to supply-chain gaps — the transition toward secure, software-defined public transit is both achievable and essential. Operators who invest now in holistic cybersecurity architectures will not only reduce operational risks but also strengthen public trust in the next generation of connected buses.